The importance of risk management cannot be understated; there are numerous risk management frameworks and certifications, and many professionals devote their entire careers to the discipline.
The ISO 27001 framework and certification includes methods that are shared by project managers, business analysts, and a variety of other disciplines. One of these methods is a process for managing risk. Risk management empowers businesses with tools and strategies to identify and mitigate threats. ISO Published a series of risk management standards, the ISO 3100 series and companies can become ISO 3100 certified in a similar manner to the process Cologix is following to become ISO 27001 certified
Risk is defined as the possibility of an unexpected event that causes an impact. While most organizations focus on negative impacts, positive impacts are also possible – such as being too successful!
Approach to Risk Management
The basic concepts of risk management are useful whether applied to information security or other endeavors that include risk. For each risk, measure the likelihood that it will occur and the expected harm that would be realized, and use those two values to calculate a risk rating. This risk rating is presented along with some other data points to communicate total risk to risk owners and business leaders.
As with any discipline that is both art and science, there are assumptions, dependencies, and constraints that impact raw measurements, which can be either quantitative (numerical) or qualitative (based on experience or “gut feeling”).
Complicated methods use both likelihood and the likelihood of occurrence, the latter bound by time. When period over period time is considered, the likelihood can either be dependent or independent. For example, a disk drive is more likely to fail as it ages (dependent) and the chance of you winning the lottery during a given week does not increase if you played on one or more previous weeks (independent). Our methodology measures independent likelihood within a one-year period and assigns a 1 – 5 rating at 20% increments, 1 being the lowest, e.g., a likelihood of 1 means a 0-20% chance within a year. Harm is also measured on a 1 – 5 scale, for brevity 1 means minimal impact and 5 is a catastrophic failure. Multiplying the two scores yields a number between 1 and 25, the rating, again for brevity, 1 means processes and controls are effective, and 25 means that we have a major problem on your hands!
Risk Register and a Risk Scorecard
The calculations and analysis stays with the risk manager(s). Risk owners and business leaders are given summaries in the form of a Risk Register and a Risk Scorecard, the two most common representations of risk.
Risk Register
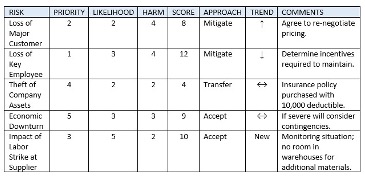
A Risk Register is a tabular view of risks. In addition to likelihood, harm, and calculated score, risk registers normally include trends, approaches, comments, and prioritization. The standard for trends is Improving, Worsening, No Change, and New, which may be depicted by the symbols ↑, ↓, ↔, and the word New respectively. The standard for approaches is Mitigate, Accept, Transfer, and Ignore, defined in the table below:
The data points are aggregated into a risk register. Once a risk has been completely addressed it is closed and removed from the risk register. If the risk register is stored in a database, closed risk records are retained, though not displayed.
Risk Scorecard
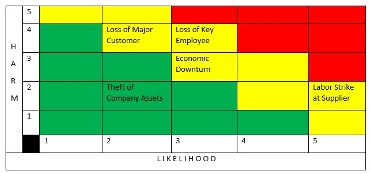
A Risk Scorecard, also referred to as a heat map, places risks on a diagram with likelihood on one axis and harm on the other. We are all accustomed to the meaning of green, yellow, and red. A risk that scores 3 for both likelihood and harm would be shown in the center cell of the chart. A consolidated picture of organizational risk can be communicated once all the risks are placed in the appropriate cells. A sample Risk Register and Risk Scorecard (with information from the sample risk register) is shown below:
 |
 |
Risk Treatment Plans
Once risks are presented, the obvious next step is determining what actions, if any, should be taken.
The work of a risk manager never ends. New risks (threats, vulnerabilities, and weaknesses) are constantly discovered. Risk management is continuously conducted, somewhat behind the scenes, and is a vital first step to determining risk treatments and countermeasures that ensure the confidentiality, security, and integrity of Cologix and Cologix customer information systems.












