Previously in the Cyber Smarts Series, we detailed the first foundational principle of the information security triad, which is confidentiality and encryption. This month we focus on the second principle, integrity.
Merriam-Webster defines integrity as the condition of being unified, unimpaired or sound in construction. A simplified information security definition (form the condition of being unimpaired) is the guarantee and evidence that information and information assets are exactly the same when transmitted, received, duplicated or analyzed. The guarantee and evidence are commonly achieved using hashing or a hash algorithm.
Hashing
While confidentiality (encryption) and integrity (hashing) may be used simultaneously, they serve different purposes, and are not interdependent. You may recall that encryption is a method of encoding which uses a cypher, and anything that is encrypted can be decrypted, and that the encoding ensures confidentiality. Hashing works a bit differently. A hash algorithm returns a fixed-length, unique signature that cannot be reversed. In simple terms, encryption is two-way (encode-decode) and hashing is one-way (encode only). The formulas are complex and may use Fibonacci Series and Prime numbers. An analogy is once again far easier to understand.
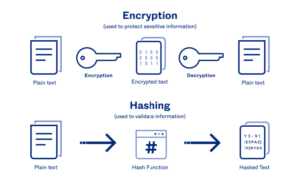
Suppose that you are asked to determine if a copy of a 300-page document is exactly the same as an original. You could conduct an exhaustive comparison of every page, which would be difficult, time consuming and prone to error. If instead, you were to count the number of upper-case letter A’s on each page. You then assign a three-digit value for each page using leading zeros, 001 to 300, then a three-digit value for the number of upper-case A’s on each page, 000 for no upper-case A’s, 010 for 10, etc. You would have a six-digit sequence for each page. If concatenated them all together in sequence, the resulting sequence would have 1,800 digits, and might look something like 001001002005003002
If the 1,800-digit sequences of both documents were exactly equal, you could conclude with some certainty that the two documents were also identical. If the words on the pages were different or the pages were out of order, you could conclude that the documents were not exactly the same. That is how a hashing algorithm works, with one important feature: each hash produced is unique. There are scenarios where the analogous example method could produce the same 1,800-digit sequence from documents that were slightly different. For example, two pages that are out of order and have the same number of upper-case A’s that would yield an identical result.
It is vital that evidence presented in criminal cases remain unaltered. This prevents forensic scientists from directly analyzing disk drives that are seized by legal authorities. To conduct forensic analysis, specialized equipment is used to create an exact duplicate of the original drives. The original and the duplicate are hashed using the same algorithm, whereby identical hashes prove an exact duplicate. The scientists then analyze the duplicate, preserving the original.
Hashing Guarantees Integrity with Passwords
Hash algorithms are also used for securing passwords. As late as the 1990s, many applications stored passwords unencrypted within database tables. This practice, which is still used by some applications, has numerous security weaknesses. Any application with the capability to provide a forgotten password is using unsecure, outdated technology and should be avoided!
Secure applications and operating systems will hash a user’s password on their local computer, encrypt the hash, transmit the encrypted hash to the server, decrypt the hash and compare the hash to the hash that is stored within the server directory. Authentication is successful if the two hashes match. While this method is more secure than sending an encrypted password, it can be defeated with some sophisticated attacks. If two users have the same password, the hashes will be identical.
This weakness was addressed in the 197Os using a technique known as “salting.” With a salted hash, unique, randomized characters known only to the client and server computers are concatenated, or linked, to the end of a password. The number of characters (the amount of salt) increases the strength and security of passwords and is configured by server and application administrators.
Get caught up on cyber security with our Cyber Smarts Series, starting with How To Change Your PIN












